Integrations
Amazon Web Services (AWS)
Gitpod is a flexible tool that works with many cloud providers, including AWS. The following page describes ways that you can integrate Gitpod and AWS.
 Read more:
Example claims in the OIDC JWT
To adjust the IAM role trust policy to restrict which workspaces can assume the role, you can define conditions keys using the name of the OIDC provider (created in step 1, e.g.
Example IAM assume role trust policy to grant access to any repo in the “gitpod-io” organization.
Read more:
You can either call the AWS CLI
Read more:
Read more:
Example claims in the OIDC JWT
To adjust the IAM role trust policy to restrict which workspaces can assume the role, you can define conditions keys using the name of the OIDC provider (created in step 1, e.g.
Example IAM assume role trust policy to grant access to any repo in the “gitpod-io” organization.
Read more:
You can either call the AWS CLI
Read more:
OIDC Integration with AWS
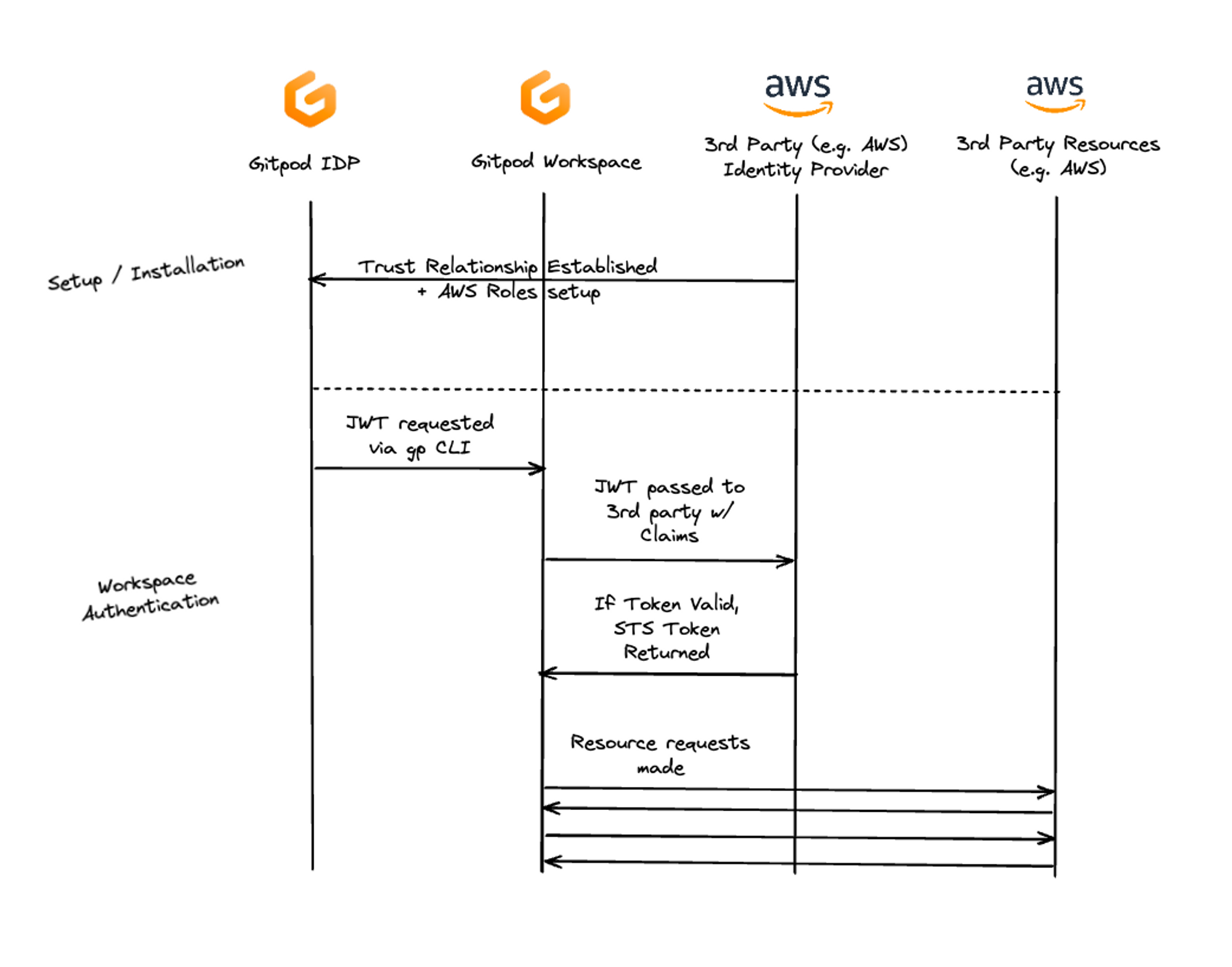
Gitpod can connect workspaces to AWS using Gitpod support for OpenID Connect, which allows workspaces to retrieve AWS access credentials in the workspace without the use of static credentials, or environment variables. In the following flow, an IAM role is created in an external AWS account, through usage of thegp command in Gitpod. The generated JWT token includes claims about the workspace and it’s owner, and is exchanged with AWS for an STS token. That STS token is related to an IAM role and will inherit any access that is given to that IAM role. Modelling the access controls is the responsibility of the AWS account owner/administrator.

Sequence diagram of Authentication via OIDC using AWS with Gitpod
Step 1: Create an “AWS Identity Provider” resource
AWS Identity Providers allow you to manage user identities outside of AWS, instead of creating IAM users in your AWS account and giving these external identities (e.g. Gitpod workspaces) permissions to use AWS resources in your account. To connect Gitpod to AWS you need to create an “IAM identity provider” to establish a trust relationship between your AWS account and Gitpod. Gitpod supports OpenID Connect (OIDC), so please follow AWS’s guide here to create an OIDC identity provider.- Configure the URL of the identity provider to:
https://services.<gitpod-installation>/idp- For an Enterprise installation running under
companyname.gitpod.cloud, the URL is:https://services.companyname.gitpod.cloud/idp.
- For an Enterprise installation running under
- The client ID / Audience should be set to:
sts.amazonaws.com
[Optional] Add
For an Enterprise installation running under
/.well-known/openid-configuration to the end of the identity
provider’s URL to see the provider’s publicly available configuration document
and metadata. For an Enterprise installation running under
companyname.gitpod.cloud, the
URL is: https://services.companyname.gitpod.cloud/idp/.well-known/openid-configuration.- [AWS docs] Identity providers and federation
- [AWS docs] Creating OpenID Connect (OIDC) identity providers
Step 2: Create an AWS role with a trust policy
Now that your AWS account is set up to trust Gitpod, you need to create an AWS IAM role that can be assumed by the Gitpod workspace user. You can restrict who has access to the assumed role based on claims in your Gitpod workspace JWT token.Important: We strongly recommend you adhere to the principle of least
privilege, and ensure that only relevant workspaces and users can assume
your AWS role.
You can inspect the claims that will be sent to AWS by running
gp idp token --decode --audience sts.amazonaws.com inside a Gitpod workspace. Pay
attention to the sub claim containing the repository URL that was used to
start that particular Gitpod workspace. This claim will be used in the
examples below.gitpod.io) followed by the claim (:aud, :azp, :amr, sub). There are some examples below that show how this works. Read more about these OIDC condition keys here.
Here are some examples restricting who can assume the role depending on the sub key contents, in this case, the repository from which a Gitpod Workspace was created.
This particular example, shows that only users that create a Gitpod Workspace from https://github.com/gitpod-io/my-application can assume this role:
Example IAM assume role trust policy to grant access only to the repo gitpod-io/my-application
The same thing happens in the following example, the only difference is that the condition changed to StringLike to consider all repositories from the https://github.com/gitpod-io/ organization. The same thing could be done to consider all branches from a respository, example: https://github.com/gitpod-io/my-application/*.
Step 3: Assume the AWS role to retrieve the AWS credentials
Important: The following assumes that your workspace has the AWS CLI
installed so that it can call
aws sts assume-role-with-web-identity.assume-role command manually, or use the helper command within the gp CLI, gp idp login aws which will automatically update your AWS CLI credentials file.
The token expiry can be customized using --duration-seconds=<token-expiry-in-seconds>, this configuration option exactly matches the --duration-seconds configuration option offered by AWS CLI. The default is 3600 seconds. Note, to use a longer expiry your AWS Administrator must allow for longer sessions.
You can add the following to your gitpod.yml to login to AWS using OIDC and then fetch a secret dynamically from AWS Secrets Manager for use in your application:
Example .gitpod.yml that assumes an AWS web identity role:
.gitpod.yml
Troubleshooting
Usegp idp token --decode --audience sts.amazonaws.com to print your workspace JWT token. Ensure that any claims against the sub match the trust policy in AWS.

