User settings
Environment Variables
You can utilize environment variables with Gitpod in the same way as you do locally. You can set environment variables at the user level, which will make them available in all your workspaces (or a specified subset of them).
Gitpod supports encrypted, user-specific environment variables.
They are stored as part of your user settings and can be used to set access tokens, or pass any other kind of user-specific information to your workspaces.
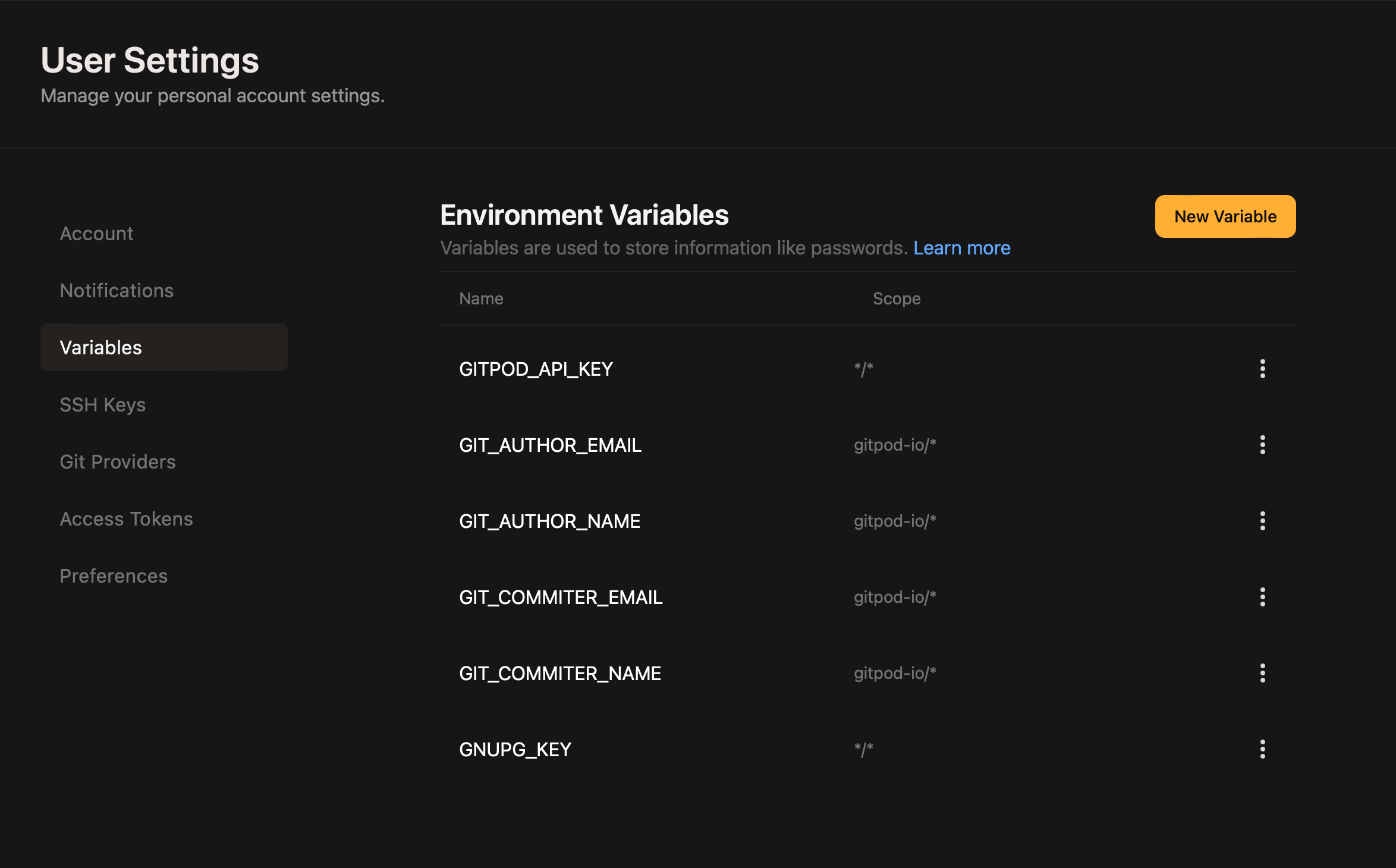 Scope is a feature of Variables that limits which organizations and repositories may use the variable values in workspaces.
Repository patterns follow the
Scope is a feature of Variables that limits which organizations and repositories may use the variable values in workspaces.
Repository patterns follow the
Using the command line:
The Workspace CLI prints and modifies the persistent environment variables associated with your user for the current repository.
To set the persistent environment variable
Beware that this does not modify your current terminal session, but rather persists this variable for the next workspace on this repository.
If you’re using the
To update the current terminal session with the latest set of persistent environment variables, use:
If you’re using the
To delete a persistent environment variable use:
Note that you can only delete/unset variables if their repository pattern matches the repository of the workspace exactly. This means that you cannot delete environment variables with a repository pattern such as
For general information on using and setting up environment variables with Gitpod, see the Environment Variables documentation.
Ways of setting user-specific environment variables
Using the account settings
You can also manage persistent environment variables in your account settings, where you can add as many environment variables as you wish.
Environment Variables in Account Settings
owner/repository pattern. You can use a wildcard on either of the parts, e.g. gitpod-io/* would make that variable available in all repositories owned by gitpod-io.
Conversely, */vscode would make that variable available on all repositories called vscode, which is especially useful for forks.
*/* makes that variable available in all of your workspaces with that exact hierarchy depth. If you want to match all repositories, no matter the depth, use */**.
Note: For GitLab, which allows to have nested group/repository structures like owner/some-group/sub-group/repo, the number of segments in the pattern has to match the number of segments in the repository name. This constraint exists to avoid surprises and leaking of content into unexpected repositories. For matching arbitrary segments to the right, there is a dedicated pattern of **.
Some example patterns (for GitLab) and results for the mentioned owner/some-group/sub-group/repo repository:
*/**: ✅*/*: ❌owner/some-group/*/*: ✅owner/some-group/*: ❌owner/some-group/**: ✅owner/**: ✅owner/some-group/sub-group/repo: ✅*/some-group/sub-group/repo: ✅
While the variable values are stored encrypted, they are available as plain text inside a workspace. Be careful when sharing your live workspace or when using
*/* or */** as a repository pattern.Using the command line: gp env
The Workspace CLI prints and modifies the persistent environment variables associated with your user for the current repository.
To set the persistent environment variable foo to the value bar use:
gp can only interact with the persistent environment variables for this repository, not the environment variables of your terminal.
If you want to set that environment variable in your terminal, you can do so using -e:
fish shell:
fish shell:
*/foo, foo/* or */*. To remove them, you can use the account settings.