Environment Variables
You can utilize environment variables with Gitpod in the same way as you do locally. You can set environment variables at repository level, which will make them available in all workspaces started on the repository in your organization.
Setting Environment Variables in repository settings
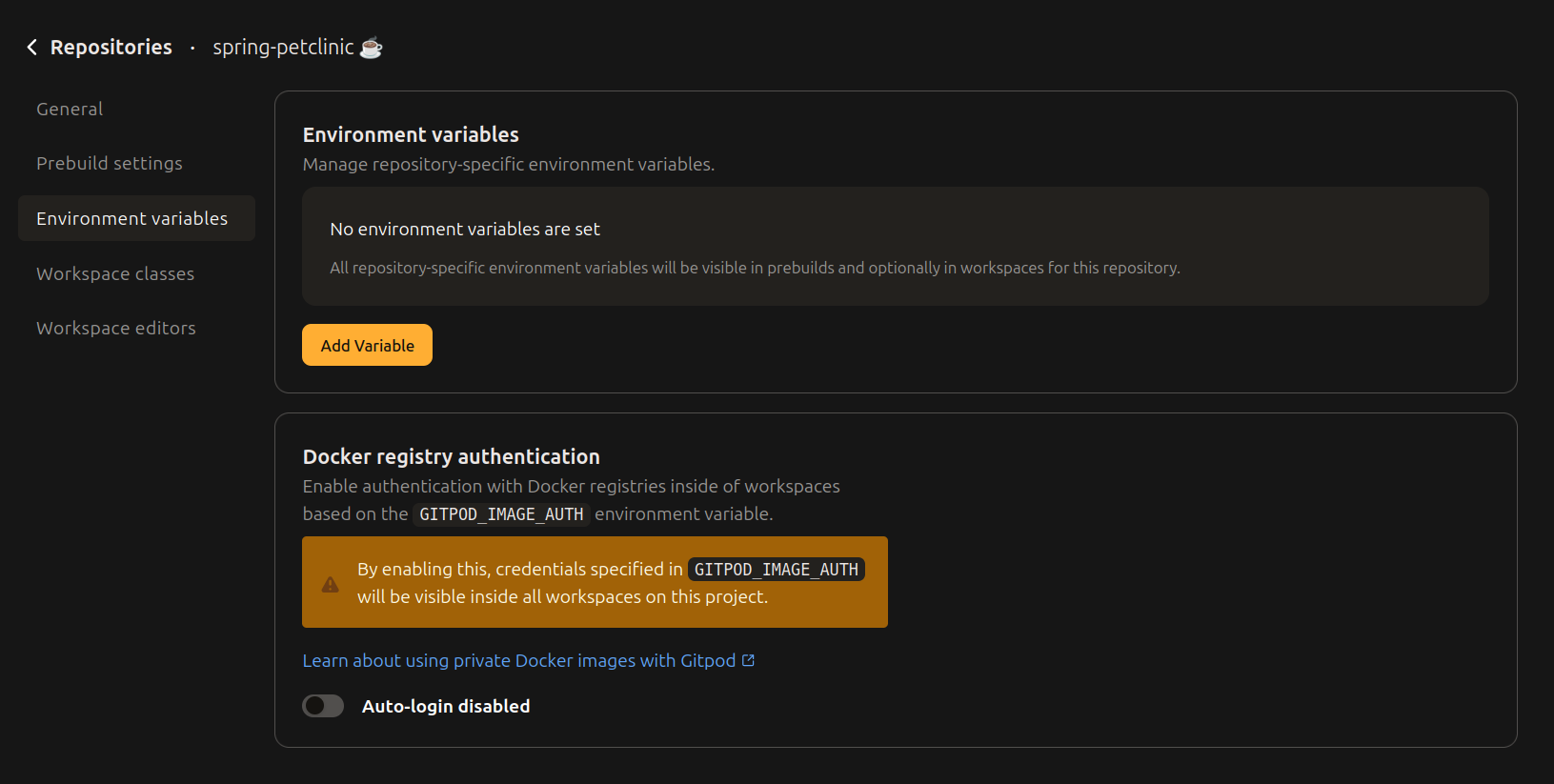
Environment Variables in Repository Settings
Repository-specific Environment Variables will take precedence over User-specific Environment Variables. Only members of the Gitpod organization where the repository resides will be able to access the environment variables inside a running workspace. Even if the imported repository is public, people outside your Gitpod organization will not have access to these environment variables.
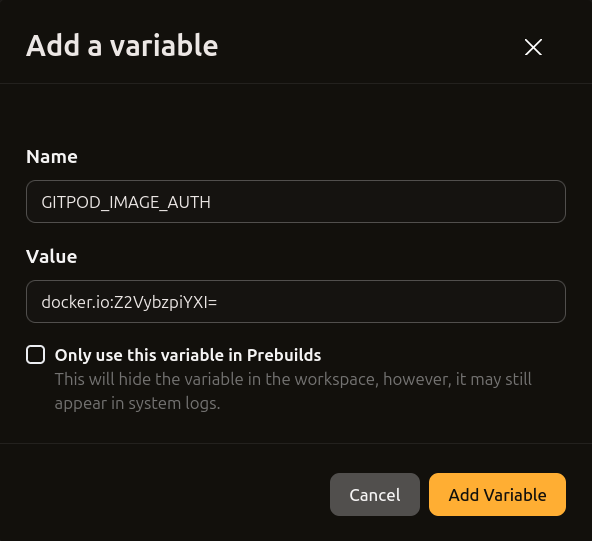
Add an Environment Variable in Repository Settings
Environment variables defined in a repositories settings will be visible in prebuilds and optionally also in workspaces. This is useful for prebuilds to access restricted services.
Setting Environment Variables in .gitpod.yml
See .gitpod.yml for more details.
Setting Environment Variables in Your Source Code
Alternatively, you can use the env property in your .gitpod.yml file to set non-secret, static environment variables. Learn more.
Repository variables defined in the repository settings will take precedence and will override variables defined in the .gitpod.yml’s env property. See the Environment Variable Prioritization Stack for more.
Docker Registry Authentication
Gitpod supports the special environment variable GITPOD_IMAGE_AUTH to configure access to private Docker registries (cmp. section “Use a private Docker image”).
By default, the environment variable GITPOD_IMAGE_AUTH is not mounted into workspaces for security reasons. If this is wanted nonetheless (e.g. to enable developers to seamlessly use docker pull / docker push, or to enable the gp validate workflow), the repository configuration has a toggle to enable that.
When it’s enabled, and GITPOD_IMAGE_AUTH is set - either on the repository or organization level -, dockerd will be configured with these credentials on workspace start. Also, GITPOD_IMAGE_AUTH is visible inside the workspace.

