Amazon Cognito
You can set up Single Sign-on (SSO) with Amazon Cognito for your team.
This section helps you to create an OIDC application with Amazon Cognito. The Client ID, Client Secret, and Issuer URL of this OIDC application are required to setup SSO in Gitpod. See the Step-by-step guide for the general instructions.
Prerequisites
As prerequisites you will need the following:
- Access to set up a new Amazon Cognito application in your AWS account.
Create an OIDC application
-
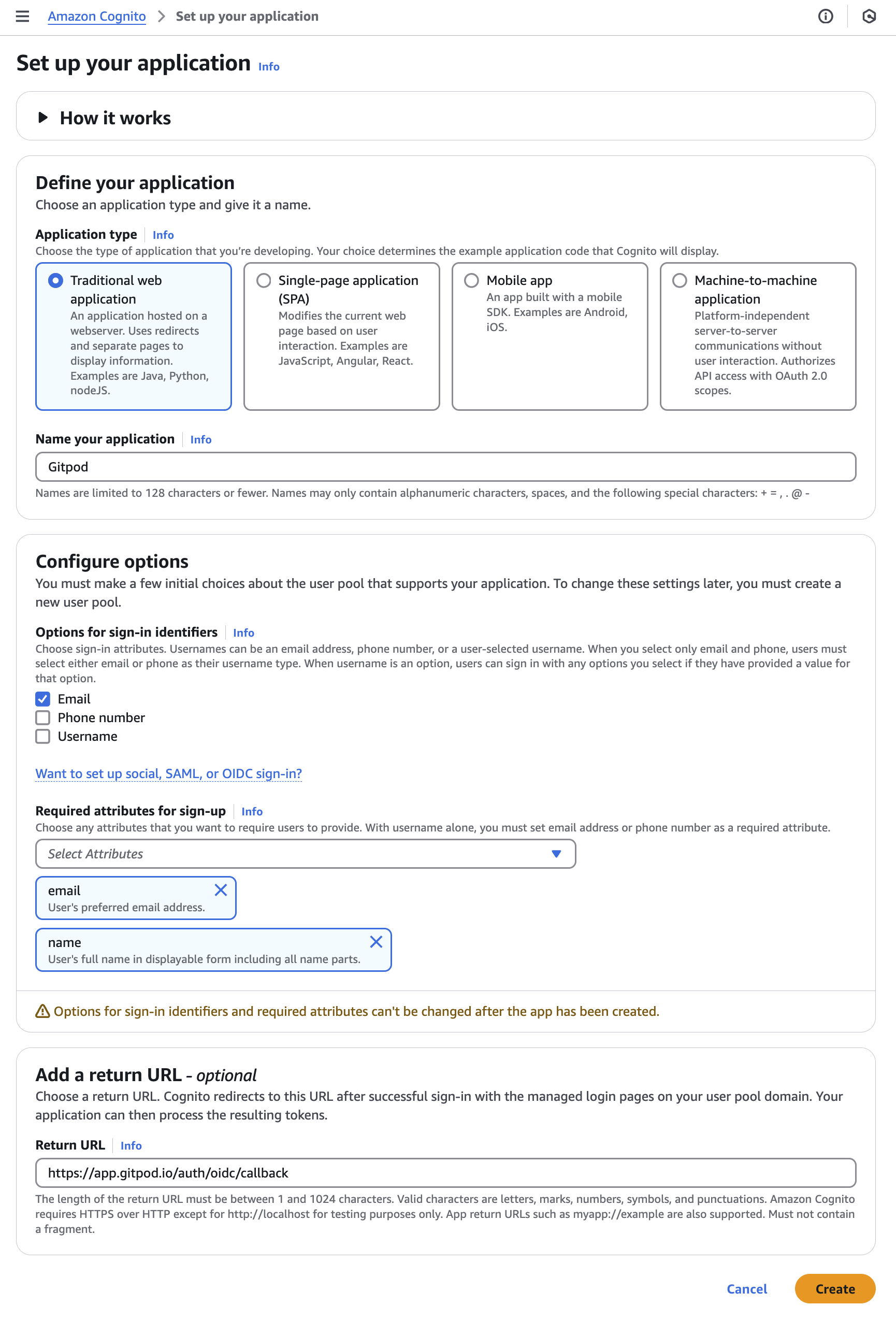
Nagivate to Amazon Cognito service page, then select
Set up your application. -
Configure the application by filling out the form:
-
Application type:
Traditional web application -
Name:
Gitpod -
Options for sign-in identifiers:
Email
-
Required attributes for sign-up:
-
email -
name
-
-
Return URL:
https://app.gitpod.io/auth/oidc/callback
Click the Create button
Amazon Cognito - New Application
-
-
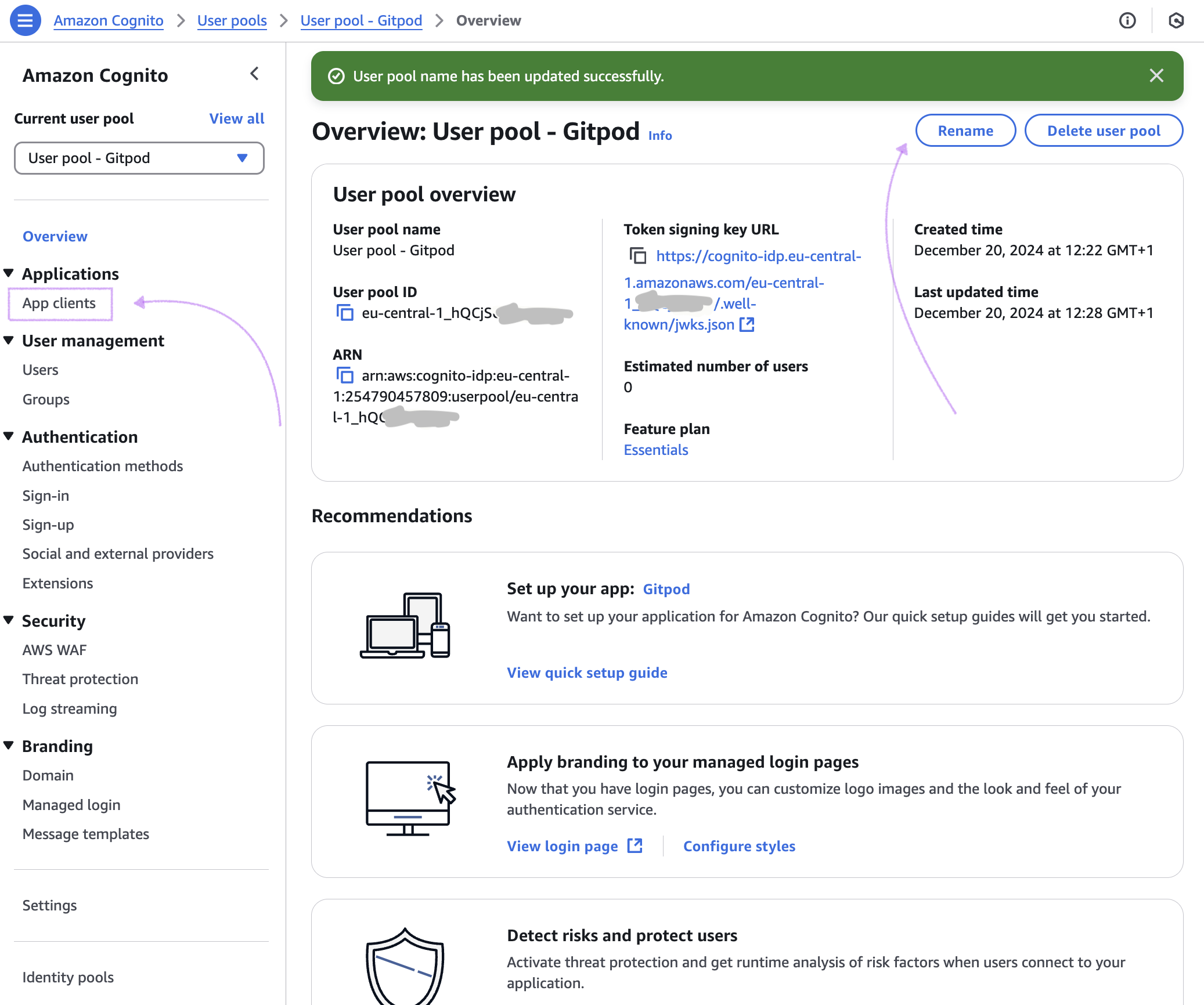
Obtain Client ID, Client Secret from the Overview page
Upon creation of the application, you will be redirected to then also created user pool. Learn more on user pools in Amazon Cognito here.
-
Feel free to rename the user pool before proceeding!
-
Obtain Issuer URL
-
You’ll find the User pool ID here
-
The pattern for the Issuer URL is:
https://cognito-idp.<awsregion>.amazonaws.com/<user-pool-id> -
Verify to use the correct URL by opening the OIDC Discovery location
<Issuer URL>/.well-known/openid-configurationin your browser, i.e. openhttps://cognito-idp.<awsregion>.amazonaws.com/<user-pool-id>/.well-known/openid-configuration.
-
-
Then navigate to Applications > App clients > Gitpod to find the details of the newly create application, and copy the information you’ll need in Gitpod:
-
Client ID
-
Client secret
-
Amazon Cognito - Overview
-
-
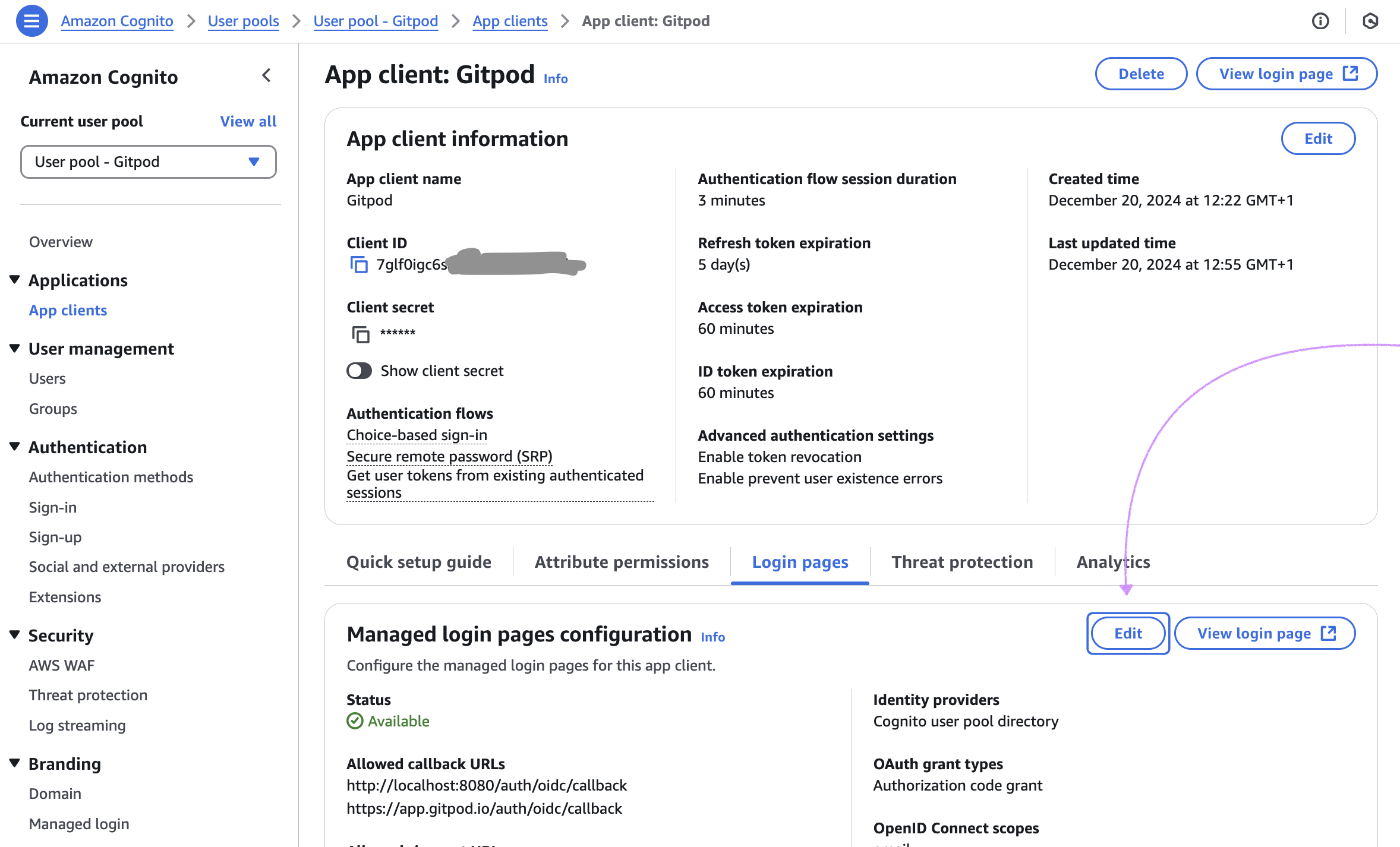
Configure OIDC Scopes
The default selection of OIDC scopes in Amazon Cognito doesn’t meet the requirements for Gitpod. Please navigate to App client > Login pages > Edit to make the necessary changes.
Amazon Cognito - Edit Scopes
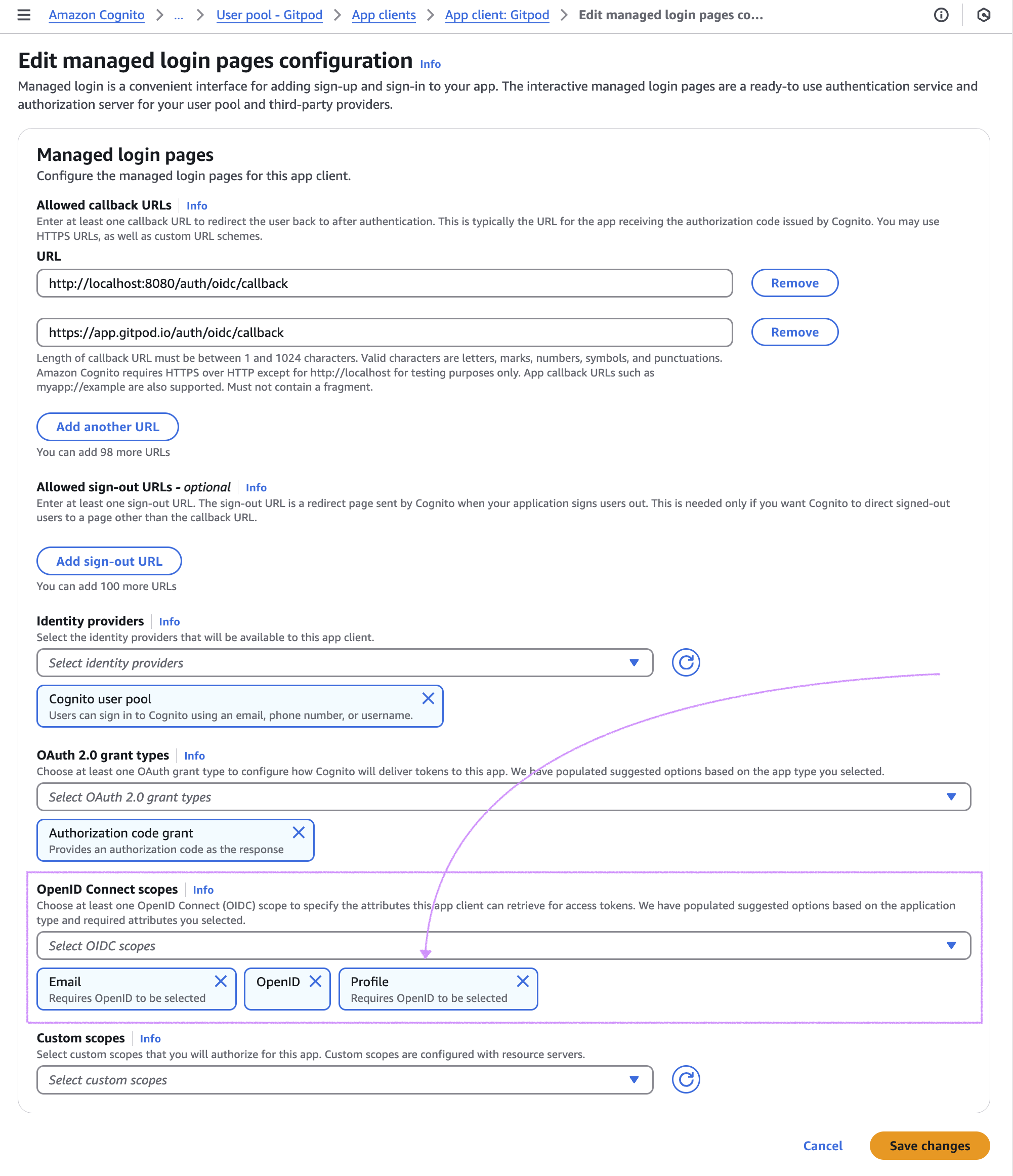
- Ensure the
Profilescope is selected here:
Amazon Cognito - Scopes
- Ensure the
-
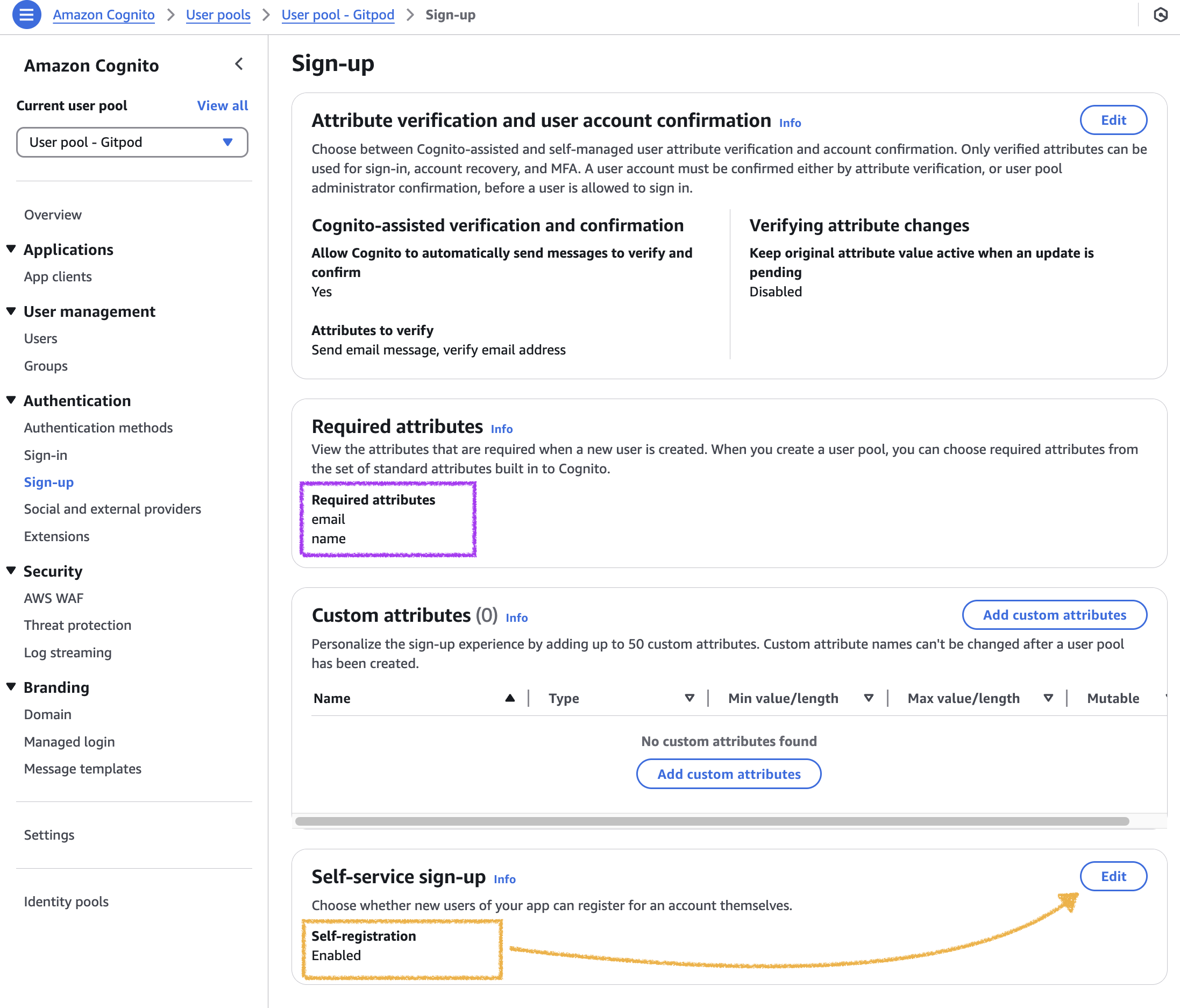
Adjust Sign-up settings to your needs
-
Disable Self-registration if you want to limit access to your application.
-
With the Sign-up disabled , you may need to manage users under User management manually.
Amazon Cognito - Sign-up
-
-
Continue with the SSO configuration in Gitpod: Clicking Save & Test

